What is Phishing-Resistant Multifactor Authentication?
As cyber threats continue to evolve, so must our defenses. While multifactor authentication (MFA) is now commonly accepted as a standard security measure for businesses, we are now seeing a need for phishing-resistant MFA due to an increase in security incidents that bypass MFA. In this blog post, we will outline how it’s different from traditional MFA and why it’s now a crucial part of businesses’ multi-layered security strategy.
MFA vs. Phishing-resistant MFA
Simply put MFA combines two or more verification methods—something you know (password), something you have (security token), and something you are (biometric verification)—to authenticate users. Traditional MFA methods, such as SMS codes or email verification, are susceptible to phishing attacks, which can intercept or spoof authentication credentials.
Phishing-resistant MFA is a security system that requires more than one method of authentication to verify the user's identity for a login or other transaction. It is designed to be resistant to phishing attacks, which are attempts to steal sensitive information such as usernames, passwords, and credit card details by disguising as a trustworthy entity in an electronic communication.
According to a recent report by Egress, 79% of organizations that fell victim to a security incident started with a phishing email, and 83% had MFA that was bypassed for the attack to succeed.
In traditional MFA, users are typically required to provide two forms of identification before gaining access to an account. Key issues with traditional MFA are:
- Traditional MFA still uses passwords as the first factor which can easily be hacked or stolen.
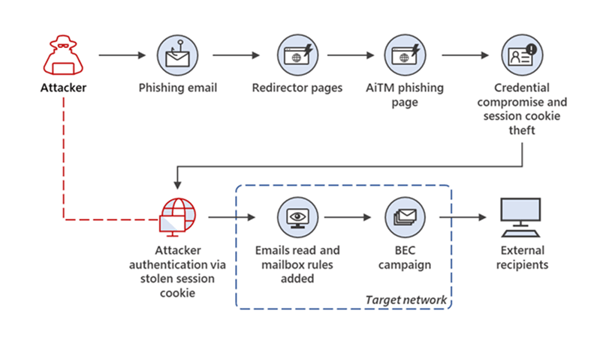
- Hackers have found ways to bypass MFA through push fatigue, SIM swap and Adversary-in-the-Middle Attacks (also known as Man-in-the-Middle attacks).
- Does not bind identities to devices so there’s no way to verify the user is who they say they are.
- Mandatory phishing-resistant MFA is starting to be mandated in certain industries.
One example where MFA isn't effective is push fatique, also known as push bombing. Cyber attackers push out a high volume of notifications to end users requesting they enter their credentials. Threat actors then use these legitimate credentials to gain initial access to victims' networks and then send a second factor to their own smartphone or other device to gain complete access.
 Implementing Phishing-Resistant MFA
Implementing Phishing-Resistant MFA
Before we dive into examples of phishing-resistant MFA, it's important to provide a list of the types of MFA solutions that are considered easily "phishable." Be weary of the following: One-Time Password (OTP) MFA, such as Google Authenticator and Microsoft Authenticator,
SMS-based MFA and push-based MFA. Phishing-resistant MFA goes a step further by incorporating additional security measures to mitigate the risk of falling victim to phishing attacks. Three of most phishing-resistant MFA methods include:
1. FIDO2 Security Keys/Tokens: (Fast Identity Online) Alliance helps promote open authentication standards, such as FIDO2, the latest standards-based passwordless authentication method. Physical devices like security tokens or smart cards that generate one-time codes can also be used as a second factor. These are less susceptible to phishing attacks compared to codes sent via SMS or email.
2. Biometric Authentication: Using biometric data such as fingerprints, facial recognition, or iris scans adds an extra layer of security. These characteristics are generally harder for attackers to replicate through phishing.
3. Certificate-based Authentication (CBA): Microsoft Entra CBA enables users to allow or require users to authenticate directly with X.509 certificates against their Microsoft Entra ID for applications and browser sign-in. This feature enables authentication with an X.509 certificate against their Public Key Infrastructure (PKI).
Implementing a phishing-resistant MFA requires proactive investment in IT strategy, planning and review starting with:
- Cybersecurity Assessment: Assess your organization’s security requirements and choose the best phishing-resistant MFA method.
- Security Awareness Training: It only takes one employee and just seconds for a breach to happen. The best approach to cybersecurity is a multi-layered one that includes Security Awareness Training. We’ve partnered with Curricula by Huntress to provide the most sophisticated phishing simulation and security user training available.
- Integrate with IT Systems: Work with your vCIO or internal department to integrate MFA with existing IT systems and user workflows.
- Enforce MFA Policies: Implement mandatory MFA for all employees who access sensitive company data.
The goal of phishing-resistant MFA is to reduce the likelihood of attackers successfully impersonating legitimate users, even if they manage to obtain some of the user's credentials through phishing techniques. It can be challenging for many businesses to effectively manage their access and security. That's where we come in! As a Managed Service Provider we will combine multiple and diverse authentication factors, alongside our standard cybersecurity solution to significantly improve security and protect your user accounts from unauthorized access. If you’re looking to learn about the best MFA for your business, reach out to us to learn more about our IT and vCIO Services.

