Sneaky Adversary-in-the-Middle Phishing Attacks
Email phishing remains one of the most common types of cyber threats targeting small businesses. But there are many different types of email phishing scams, some more advanced than others and one which we’ve recently seen an increase in: Adversary-in-the-Middle (AiTM) phishing attacks, made possible with the growing popularity of AiTM phishing kits and the alarming sophistication of global threat actors. In this blog post we’ll explain what it is and how your business can avoid it.
What is an Adversary-in-the-Middle Phishing Attack?
An AitM attack is when a bad actor intercepts and modifies communications between two parties to steal sensitive information, such as financial data or login credentials. As always is the case in email phishing threats, the hacker initiates communication via email, luring end-users into clicking malicious links and then entering credentials on fraudulent websites.
Stolen or compromised credentials were the primary attack vector in 19% of data breaches in 2022. - IBM
In July 2022, Microsoft reported that AiTM attacks targeting Microsoft 365 users were able to bypass Multifactor Authentication (MFA) to steal session cookies and gain access to victims’ Office 365 accounts.
How does it Work?
Session cookies are cookies that temporarily store data during a web session. They are small text files that can be sent to your server every time you click on a new webpage which gives certain parties the ability to monitor your activity. In the illustration below you can see the flow of an AiTM attack.
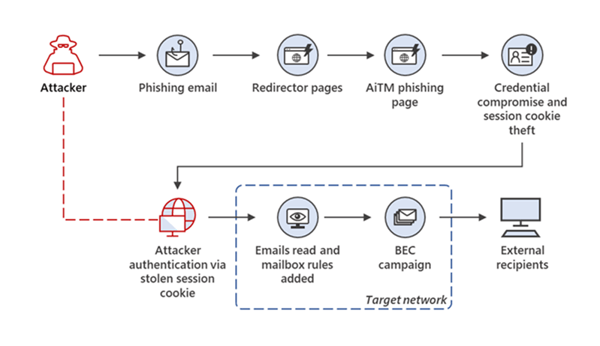 What we’ve seen among our Microsoft 365 users is the attackers ask them to open a SharePoint file shared with them from what on a surface-level appears to be a legitimate source. The file link takes them to a different domain and if the user clicks on the “view document” link, they are then directed to a false Office 365 login page which prompts them for credentials. When the user enters their credentials, including their MFA code, the attackers have immediate access to their credentials.
What we’ve seen among our Microsoft 365 users is the attackers ask them to open a SharePoint file shared with them from what on a surface-level appears to be a legitimate source. The file link takes them to a different domain and if the user clicks on the “view document” link, they are then directed to a false Office 365 login page which prompts them for credentials. When the user enters their credentials, including their MFA code, the attackers have immediate access to their credentials.
What is particularly significant about the attacks targeting Microsoft 365 users is that the bad actors can bypass several types of MFA. The cybercriminal uses a proxy server to communicate with Microsoft and host a fake login page. When the victim enters their login info, it will then steal the session cookie to provide false authentication, allowing the attacker to bypass forms of MFA, like the six-digit time-based one-time password.
Octo Tempest and Advanced Social Engineering
Of serious concern is the group tagged by Microsoft as Octo Tempest, also known as 0ktapus and UNC3944. Their extensive knowledge of technology solutions, deployment of a variety of sophisticated techniques combined with the fact that they are native English-speaking has contributed to the group's ability to gain entry into environments quicker than ever seen before.
The group is known to do in-depth reconnaissance prior to engaging potential victims. They will go as far as impersonating staff and new employees to trick IT or helpdesk into resetting credentials...Octo Tempest has also proven to be adept at bypassing MFA, both via direct social engineering and through AitM phishing attacks. -eSentire
Microsoft and security professionals around the world have dubbed the threat actor as one of the most dangerous cybercriminals. For more information on Octo Tempest and their tactics visit Microsoft's website.
How to Protect your Business from AiTM Attacks?
Common defense practices used against all phishing attacks can help protect your business from AiTM attacks. Employees need to be continue to be vigilant of any email where the sender urges the user to click on a link or log into an account, even if the sender claims to be a trusted individual. If one isn’t expecting a file, ignore the request. We always recommend adopting a multi-layered approach to cybersecurity; a strategy that combines user education with advanced security technology. Here’s the most important security measures your business can adopt to prevent a successful AiTM incident:
- Security Awareness Training that includes recent information on new tactics, such as AitM and QR code scams.
- Do not click on unknown links or visit webpages that you have never visited before to complete a login process. Use the same process to login to services and if the process changes, reach out for confirmation from IT Support before proceeding.
- Pushed-based MFA Number Matching Microsoft Authentication (now being forced beginning in May 2023).
- Complement MFA with conditional access policies, such as limiting access to managed devices and block known malicious indicators.
- Partner with a Managed Service Provider (MSP): MSPs can provide your business with advanced monitoring, automatic alerting/blocking of malicious websites, Microsoft 365 policy administration and more.
If you’re concerned about email phishing or any aspect of your cybersecurity at your business, please reach out to us.

