MasquerAds
|
Security
Cybercrime is constantly evolving. This week, we want to bring your attention to a relatively new threat: MasquerAds. Threat actors are now leveraging Google Ads, other legitimate software, and file-sharing brands to execute their malware. More care should be taken before clicking on ads (sponsored content) to avoid the MasquerAds threat.
What is a Masquerade Attack?
Masquerade attacks deploy a variety of different tactics, but generally such an attack can be described as any threat that uses a fake identity to gain unauthorized access to personal information or a computer through what appears to be legitimate sources. In the case of MasquerAds, Google ads are leveraged to trick users into downloading files that appear legitimate but contain malware.
Common risks associated with masquerade attacks include:
- Data breaches
- Sensitive/proprietary information is leaked
- Ransomware attacks
- Identity theft
- Critical system files are modified
- Users are locked out of their accounts
- Internet traffic is rerouted to malicious sites
- The download and installation of malware
How MasquerAds Works
Under MasquerAds, threat actors create domain names whose URLs are at least one letter off from the original brand. This is what is known as a typo-squatted domain, a type of social engineering attack which targets users who are tricked into visiting a website with URLs with “typos” or common misspellings of legitimate websites. Once a user clicks on a MasquerAd, they land on a phishing website that includes a download link to the malicious software. The downloadable files are typically hosted on Dropbox, Google Drive, Discord CDN, or Github.
Below is an example of a search term with the corresponding MasquerAd example:
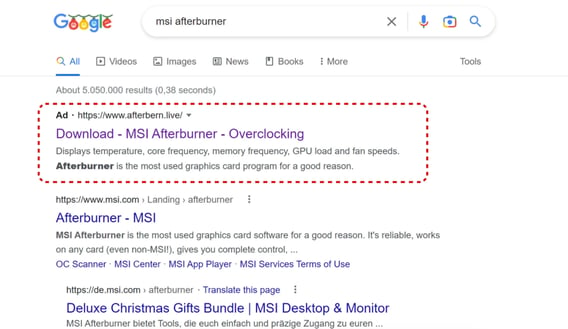
The reality that MasquerAds makes use of well-known brands, like Google and Dropbox, to deliver the threat makes it appear even more legitimate in the eyes of an unsuspecting browser.
How to Protect Against it
Small and medium-sized businesses need a multi-layered cybersecurity defense. To protect against MasquerAds, a layered approach needs to incorporate cybersecurity training, security best practices, policies and tools.
User Education: Ads at the top of search engine results are not all bad but users need to be more aware and ensure that the link they are clicking is indeed legitimate. If in doubt just skip the ad results and scroll further down the search results to click on the legitimate link.
Expert investigation of this threat revealed that many malware scanners failed to detect suspicious malware in the MasquerAds. This demonstrates just how important user education on the different tactics threat actors deploy to lure users to malicious web pages, ads and documents. Threats like these are best mitigated with annual cybersecurity training.
Security Policy: Another way to avoid this threat is to restrict employees from downloading executable files.
Endpoint Detection and Response (EDR) and Next-Generation Anti-Virus (NGAV): Employing EDR and NGAV could help prevent MasquerAds by providing protection across all endpoints. Nucleus offers both EDR and NGAV with the following features:
- 24x7x365 protection no matter where endpoints reside
- Threat hunting
- Multi-signal visibility and response across endpoint, log, network and cloud
Our multi-layered Managed Security Services help protect businesses against the ever-evolving cyber threat landscape. Deploying a variety of security services, we customize our solutions to meet your business and/or industry needs. To learn more about Nucleus’ end-to-end cybersecurity services visit our IT services web page or contact us to schedule a meeting.

