M365 SCuBA Guidelines for Small Business Cloud Security
|
Security
We regularly incorporate cybersecurity frameworks and standards into our best practices, security assessments and projects. We’ve shared how CIS Controls, NIST 800-53 and MITRE ATT&CK inform our Cybersecurity Scorecards and this week we want to draw attention to a relatively new set of security standards: Microsoft 365 (M365) Secure Cloud Business Applications (SCuBA).
In October 2022, the United States Government organization CISA (Cybersecurity & Infrastructure Security Agency) released their draft version 0.1 of their M365 SCuBA. This set of security standards provide step by step instructions for M365 security baselines. While the target audience for this document is the US Government Federal Civilian Executive Branch, it serves as a valid security guideline for small businesses to get the most out of their M365 licensing.
What Does SCuBA Cover and Why it Matters? (who is naming these things?!)
With more and more businesses relying on cloud solutions, threat actors are continuously finding new and creative ways to breach organizations. Microsoft applies monthly updates to their M365 and Azure environments that add new user facing features and strengthen our ability (as your Managed Service Provider, MSP) to configure M365 to defend or reduce the surface attack area. SCuBA outlines some of the most important security configurations we can adopt to get better protection.
While some of the security features listed in SCuBA are only available in higher license types, like M365 Enterprise E5 (which is currently $73 CAD/user/month or as an Azure AD P2 add-on at $11.50/user/month). Many of these recommendations have a slimmed down version that can be configured within Microsoft 365 Business Premium. Four key security features we recommend incorporating from SCuBA are:
- Conditional Access
- Microsoft Identity Protection
- Multifactor Authentication (MFA)
- Role-based Access Control (RBAC)
Conditional Access
Conditional Access is what it sounds like: conditions have to be met before a user is allowed access. Geoblocking allows you to restrict access based on a user’s geographic location. For instance, if your users are only ever in Canada, you can block access from all other countries. You may also set conditions of when MFA is triggered. If a user is in a trusted site, such as your office, then they can login without MFA. However, if a user is outside the office, then they would be required to authenticate with MFA.
Microsoft Identity Protection
Microsoft Identity Protection can also be configured (using the M365 E5 license) to watch user behaviour and identify risk. Some common examples are anonymous IP addresses trying to log into the system or a user that was in Ottawa on Monday morning but now showing logins from Japan on Monday afternoon, etc. This would trigger a different response, such as requiring an MFA prompt or even outright blocking the user from logging in.
Multifactor Authentication
Not all MFAs are created the same. SMS and Voice MFA are not best practices and should be avoided at all costs. SIM swapping is not that hard and can be used to change your cell phone to someone else’s mobile device who will then receive those calls and texts. Check out this video demonstrating just how easy social engineering can be:
Just last month, Microsoft has added functionality to Microsoft Authenticator that not only lets you click ‘yes’ or ‘no’when prompted for MFA, but will also show you the name of the application, a map with the location from where the request came from, and ask you to type a number into your phone that matches the number showing on your screen. This enhanced MFA helps protect against threat actors that are able to get into your system and are hoping that you just click‘yes’ every time the MFA app prompts.
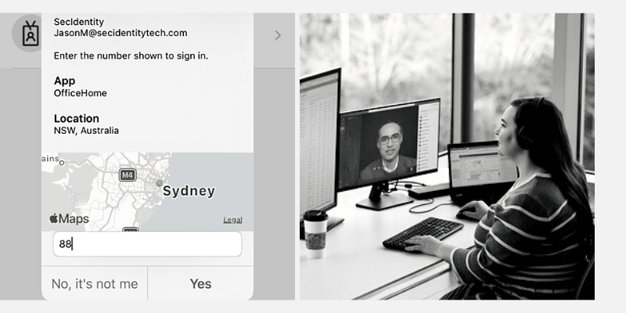
Further to this, Windows Hello for Business is now becoming a security standard many will get behind. We unlock our phones with our face and now we can unlock our machines with our face. All laptops come with front facing cameras, however a smaller subset of them come with a front facing camera which also has infrared. If this camera has infrared, it can be used for Windows Hello. Just look into the camera with the infrared, your face will be scanned and you will be let into your device. No muss, no fuss.
We are moving to a password-less world as passwords have long been the weak spot in protecting our IT environments. By using these additional features, like facial recognition or number matching, the reliance on passwords is declining and we welcome that!
Role-based Access Control (RBAC)
RBAC is an access-control mechanism defined around roles and privileges. It ensures that users only have access to the systems they should have access to. While it’s easiest to just give admin rights to everyone to allow them access to what they need, this could result in a risk no business ever wants to take: if one user is compromised, everything is compromised.
If an engineer needs access to HR forms, projects they are working on and access to the time tracking system, then they should only have access to those and not have access to executive files, salary information, or backend administrative access to servers that allow for changes to be made.
This policy is common sense and has been a standard for decades. With the advent of cloud systems and different cloud based applications, some of these systems have been slower to catch onto RBAC. All mature cloud application providers have this standard baked in, but it’s still a best practice to ensure that users have access to only what they need to.
The SCuBA document covers RBAC best practices for M365, which include: limiting guest access and limiting access to set time periods. For example, if you have a vendor that you’ve authorized to have access to your Great Plains Software to make updates over the next two weeks. Their access should be limited to 15 days and set to auto-expire. There would be no reason, in this example, for that vendor to have permanent access to your systems going forward.
As a Managed Service Provider we have a responsibility to continuously review our Clients’ security as well as our own internal security to ensure that we are aligned with leading security standards and frameworks. While we may not be able to incorporate all aspects of SCuBA into your business, we can make recommendations on what we can integrate with your M365 licensing. If your business is concerned about your security maturity, please reach out to us.


