What is a Homoglyph Domain Attack?
In the ever-evolving landscape of cybersecurity, threats continuously change and hackers find new ways to exploit vulnerabilities. One such method is the use of homoglyph domains. Homoglyph domains involve the substitution of visually similar characters to deceive users and evade detection. This blog explores the intricacies of homoglyph domains, their potential risks, and strategies to mitigate these cybersecurity threats.
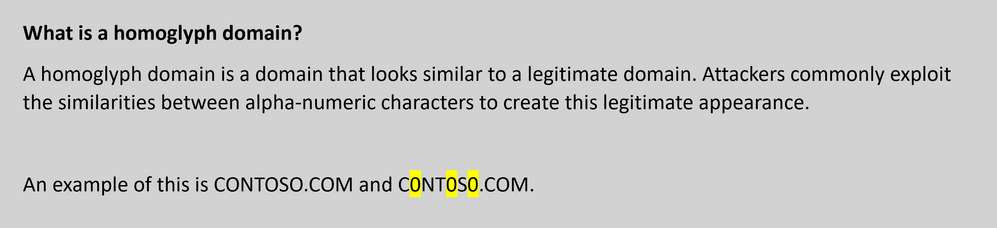
Homoglyphs are characters that look similar or identical but have distinct Unicode code points. Cybercriminals leverage these similarities to create deceptive domain names that closely mimic legitimate ones. The most common example is substituting the letter 'o' with the number '0' or using characters from different alphabets that resemble familiar letters.
The Risks Associated with Homoglyph Domains
Phishing Attacks: Homoglyph domains are frequently used in phishing campaigns to trick users into revealing sensitive information such as login credentials, financial details, or personal data.
Malware Distribution: Cybercriminals use deceptive domains to host malicious content, including malware, ransomware, or other harmful software. Users who unknowingly visit these sites may expose their devices to serious security risks.
Brand Impersonation: Homoglyph domains enable attackers to impersonate well-known brands, leading users to believe they are interacting with a legitimate website. This can damage the reputation of the targeted brand and result in financial losses for both the brand and its customers.
In July 2021, the Eastern District of Virginia issued a court order requiring domain registrars to disable service on the malicious domains, which included “thegiaint.com” and “nationalsafetyconsuiting.com,” which were used to deceive Microsoft customers.
How to Mitigate Homoglyph Domain Threats at your Small Business?
Cybersecurity Awareness Training: Training employees to recognize homoglyphs and be cautious about clicking on links from unfamiliar sources can significantly reduce the risk of falling victim to homoglyph domain attacks and other social engineering scams. Learn more about our Security Awareness Training on our website.
Microsoft 365 Defender: Microsoft 365 Defender can now automatically disrupt advanced homoglyph attacks using Extended Detection and Response (XDR) signals across endpoints, identities, email, and SaaS apps to stop attack progression and limit the impact to organizations.
Managed Detection and Response (MDR) for Microsoft 365: MDR is a security software solution that is backed by real people, a Security Operations Center (SOC) team that is solely dedicated to protecting a businesses’ Microsoft 365 environment. It integrates seamlessly with businesses’ Microsoft cloud environment to collect and analyze user, tenant and application data to more precisely review anything deemed suspicious and remediate threats quickly.
Homoglyph domains represent a sophisticated cybersecurity threat that demands heightened awareness and proactive measures. As cybercriminals continue to refine their tactics, we must remain vigilant. By adopting a multi-layered approach that combines education and technology, we can collectively mitigate the impact of homoglyph domain attacks and strengthen our defenses against evolving threats. Contact us to learn about our Managed Security Services.

