Amazon Prime Phishing
A few months ago, I wrote a blog about my experience with an attempted phishing attack where the fraudster pretended to be the CEO of Nucleus. The blog received a lot of positive feedback due to the apparent legitimacy of the phishing attempt. It was not your average phishing/ spear-phishing email, it was more sophisticated.
Well, my work email was once again targeted with another phishing attack that is even more unique and advanced than I’ve seen before.
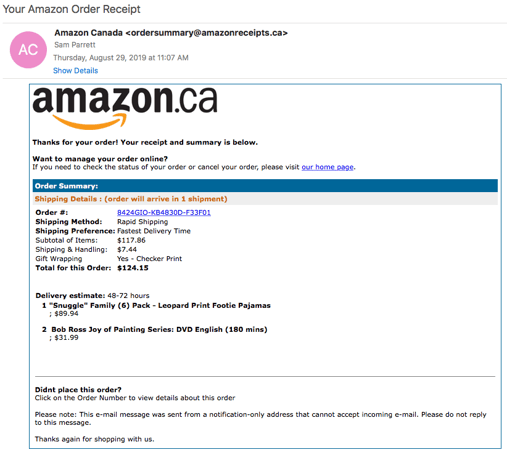
I saw in the subject line that the email appeared to be from Amazon and since I was expecting a package, I was eager to click into it.
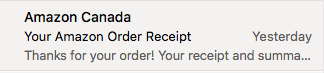
Upon first glance, the email looked normal: the right colours, the right spelling, and the right components one would expect to see from an Amazon order email. It wasn’t until I saw the order details that I knew this wasn’t an email regarding anything I have ordered. 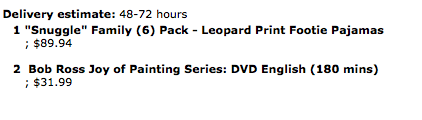 While I, like many people, am a fan of Bob Ross…the footie pyjamas and Bob Ross DVD was not anything I had ordered. My first thought was, “this must be someone else’s order and I received their email by accident.” However, working with a team at Nucleus who are very diligent with instilling cybersecurity knowledge into us, I knew that this was actually a phishing attempt and not a human error.
While I, like many people, am a fan of Bob Ross…the footie pyjamas and Bob Ross DVD was not anything I had ordered. My first thought was, “this must be someone else’s order and I received their email by accident.” However, working with a team at Nucleus who are very diligent with instilling cybersecurity knowledge into us, I knew that this was actually a phishing attempt and not a human error.
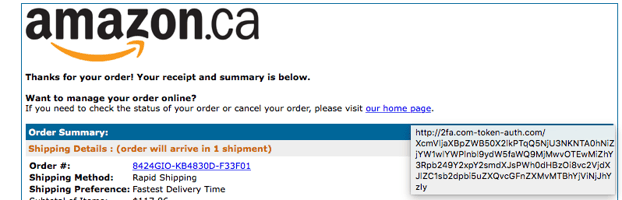
One of the tips we teach our clients with emails that appear suspicious is to hover over any hyperlinks in the email to see where clicking on the link would take you. Hovering over the “visit our home page” link clearly shows you will not be taken to the Amazon Homepage.
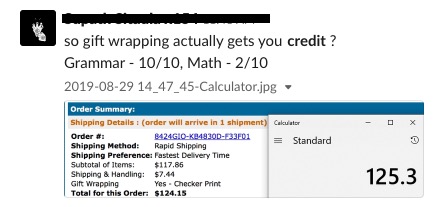
That was enough for me to report the email as phishing and let our team know. There were other details in the body of the email that proved this was not legitimate such as improper math as pointed out by one of my coworkers. Sloppy work on behalf of the attacker.
Another tip we give to our clients is to check the email domain of the sender. It should match the domain of the website of the company. For example, any email from Amazon should end in “amazon.ca/com”. For example, “order-update@amazon.com” is a real email address. The email address from my sender was “ordersummary@amazonreceipts.ca.” Not a real Amazon email.
In a lot of cases, these phishing attempts have grammatical errors which make them easier to identify. However, this Amazon spoof was well executed and did not display any obvious errors.
Luckily, because of the training I received at Nucleus, I did not click any links and instead, reported the email as phishing.
It would be understandable if someone without cybersecurity education fell for the spoof and ended up clicking links, or replying to this email due to its apparent realism. With these more sophisticated attacks showing up more and more in the news, we are proud to offer our clients Cybersecurity Awareness Training, to empower them with skills to detect attempted attacks. If you are interested in equipping your team with an education that helps prevent potential attacks, please reach out to us to learn more about how we can help protect you and your data!


